TL;DR: The Misconfiguration Manager DETECT section has been updated with relevant guidance to help defensive operators identify the most prolific attack techniques from the Misconfiguration Manager project.
Background
If you have been following SpecterOps’s offensive security research over the last few years, you may have noticed our interest in targeting attack paths leveraging Microsoft’s Configuration Manager (CM), formerly known as System Center Configuration Manager or SCCM. At SO-CON 2024, Duane Michael, Chris Thompson, and Garrett Foster released the Misconfiguration Manager project, which represented a knowledge base of offensive techniques. Additionally, the project contained a large list of preventive controls complemented by a small list of detective controls that I had put together for the launch of the project. You can read more about the original attack and defensive techniques from the project launch on Duane’s blog, Misconfiguration Manager: Overlooked and Overprivileged. This project grabbed my attention before launch due to its relatability to my network operations background. As many security researchers began this career path, I started my career in customer support and eventually found myself in system administration. Many years ago, I can remember learning how to deploy security patches, software, and operating systems via SCCM. One lesson that stood out to me was this understanding that access to SCCM was to be guarded due to the power this management tool had within the entire Active Directory domain. Once implemented, SCCM managed the whole domain with high levels of privilege and the SCCM console acted as a central point of administration. Fast-forward many years, I was happy to help document detections for this project and give defenders a chance to detect the prolific attack techniques targeting Microsoft’s Configuration Manager. My goal was to give the current industry the tools that I needed when I was responsible for guarding the use of SCCM.
DETECT-4
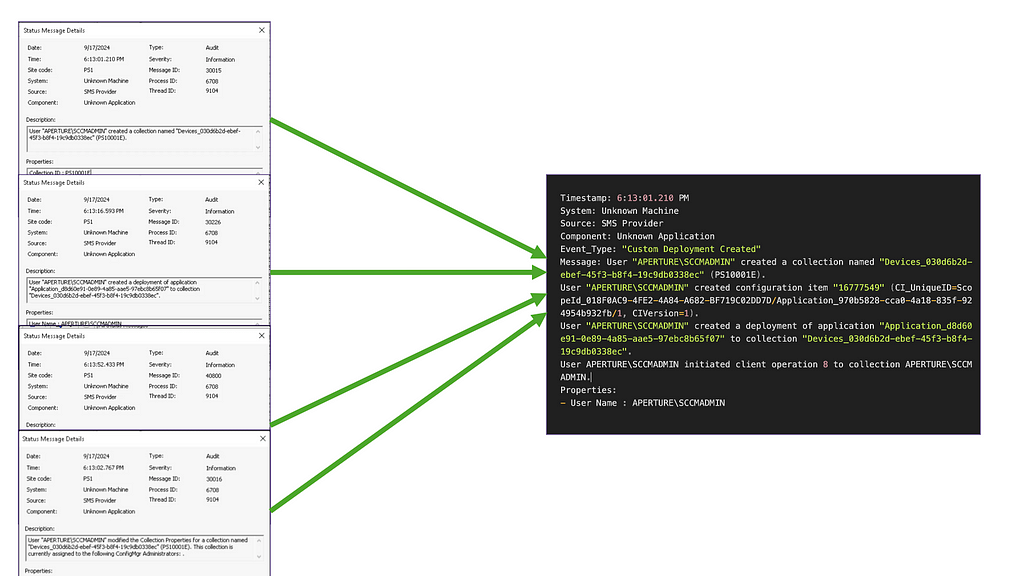
DETECT-4: Monitor App Deployments via Status Message Queue Configuration Manager can deploy applications to domain-joined and non-domain-joined clients within the scoped environment. These application deployments need only to reference a UNC path, which opens quite a wide gate to where the application can be sourced. Applications can be locally hosted on the targeted client machine, stored within a remote hosted share, or uploaded and hosted within Configuration Manager, itself. Luckily, Configuration Manager maintains the Status Message Queue log that queries the backend Configuration Manager MSSQL database and returns the plain text verbiage of each application deployment. Defenders can ingest these status messages into a centralized logging solution (Elastic, Splunk, etc). The logs without the corresponding MSSQL database returns are located on the Site Server’s smsprov.log file. There are several open-source projects that aid in collecting the status messages and most of them will require configuring DB Connect at some point to match the collected SMSProv log to the MSSQL returns to get the full event ingested. Once ingested, defenders can use this data source to build a composite event identifying the collection creation (Message: 30015) or the modification of a collection (Message: 30016), the creation of a deployment (Message: 30226), and the initiation of the deployment (Message: 40800).
DETECT-5 and DETECT-6
DETECT-5: Monitor Group Membership Changes to SMS Admins Group DETECT-6: Monitor Group Membership Changes for RBAC_Admins Table The SMS Admins security group and the RBAC_Admins table represent the local security group with access to the SMS Provider, a WMI provider with write access to Configuration Manager (CM) databases. When a Full Administrator is added via the console or directly through modifications to the RBAC_Admins and RBAC_ExtendedPermissions tables in the site database, the account gets added to the local SMS Admins group on computers hosting the SMS Provider role. Defenders can leverage object access auditing to identify modifications to the local security group SMS Adminsindicating a new member has been maliciously added/removed (Event ID: 4732 [Add] or Event ID: 4733 [Removed]). Ideally, an organization would not frequently change this local security group. A custom SQL audit must be created from the Configuration Manager MSSQL database to target the modification to the RBAC_Admins table and generate the event within an event provider. For the example in DETECT-6 , I chose to forward the event to the Application log. When the modification occurs, an SQL Audit Event (Event ID: 33025) will be generated with the data containing the INSERT that occurred in RBAC_Admins table.
Audit event: audit_schema_version:1event_time:2024-10-23 03:11:01.1300947...snip...session_server_principal_name:APERTURE\ATLAS$server_principal_name:APERTURE\atlas$...snip...object_name:RBAC_Adminsstatement:INSERT INTO RBAC_Admins (AdminSID, LogonName, IsGroup, IsDeleted, CreatedBy, CreatedDate, ModifiedBy, ModifiedDate, SourceSite) SELECT 0x0105000000000005150000007D2E52AA5AD54377C5FC12F357040000, 'APERTURE\testsubject1', 0, 0, '', '', '', '', 'ps1' WHERE NOT EXISTS ( SELECT 1 FROM RBAC_Admins WHERE LogonName = 'APERTURE\testsubject1' )...snip...
DETECT-7
DETECT-7: Monitor Read Access to the SMSTemp Directory Configuration Manager implementations can utilize a preboot execution environment (PXE) to deploy pre-configured gold-image operating systems to target clients within the environment. The components that enable this capability typically involve Distribution Points that contain domain credentials within PXE media. The Distribution Point will host a REMINST (Remote Install) share that contains PXE boot variable files within an SMSTemp directory. System Access Control List (SACL) can be set on the SMSTemp directory (Event ID: 4663) and the related PXE variable files that offensive tooling will scrape to find domain credentials.
Event ID: 4663An attempt was made to access an object.Subject: Security ID: SYSTEM Account Name: ATLAS$ Account Domain: APERTURE Logon ID: 0x3E7Object: Object Server: Security Object Type: File Object Name: C:\RemoteInstall\SMSTemp\2024.09.07.09.10.30.0001.{7CEC8AFB-6AD5-45C1-A6E2-433D7F4D2E71}.boot.var Handle ID: 0x528 Resource Attributes: S:AIProcess Information: Process ID: 0xfbc Process Name: C:\Windows\System32\svchost.exeAccess Request Information: Accesses: ReadData (or ListDirectory)
Additionally, Detailed File Share auditing (Event ID: 5145) enabled on the Distribution Point will monitor for connections to the REMINST file share. YMMV on the verbosity of enabling this particular audit category”Š”, “Šbut as defenders we typically have the power to filter at the data shipper level.
DETECT-8
DETECT-8: Monitor Connections to Winreg Named Pipe The use of the \\.\winreg named pipe can be used to query Configuration Manager infrastructure to obtain reconnaissance on PXE configurations or general Configuration Manager implementation details. The protocol is implemented on top of DCERPC, and can be detected via Zeek DCERPC logs or more specifically auditing the Detailed File Share events on Configuration Manager infrastructure. Additionally, Microsoft Sysmon Operational logging contains Named Pipe Connections (Event ID: 18) which can be used to identify the general use of the \\.\winreg named pipe.
Event ID: 18Pipe Connected:RuleName: -EventType: ConnectPipeUtcTime: 2024-10-24 15:02:05.541ProcessGuid: {8288158a-ce46-66cf-eb03-000000000000}ProcessId: 4PipeName: \winregImage: SystemUser: NT AUTHORITY\SYSTEM
DETECT-9
DETECT-9: Monitor Local Object Access for SCCM Logs and Settings The Misconfiguration Manager project has multiple methods of remotely enumerating Configuration Manager site information. However, the Configuration Manager settings can be enumerated locally if the adversary has control over a Configuration Manager-managed client. Typically, a Configuration Manager-managed client will have the following directories: C:\Windows\CCMCACHE C:\Windows\CCMSETUP C:\Windows\CCM\Logs These directories can be triaged for the DNS names of the site servers, distribution points, and management points. Additionally, the registry key/value HKLM:\SOFTWARE\Microsoft\SMS\DP\ManagementPoints will enumerate the Distribution Points and Management Points for that particular Configuration Manager-enrolled client. Defenders can enable custom auditing on these directories and their child files. Defenders can also set SACLs on the registry key and the related child value ManagementPointsvia SACLs (Event ID: 4663).
Event ID: 4663An attempt was made to access an object.Subject: Security ID: APERTURE\TESTSUBJECT1 Account Name: TESTSUBJECT1 Account Domain: APERTURE Logon ID: 0x7FE94DObject: Object Server: Security Object Type: File Object Name: C:\Windows\CCM\Logs\CcmMessaging.log Handle ID: 0x4a4 Resource Attributes: S:AIProcess Information: Process ID: 0x1594 Process Name: C:\Tools\SharpSCCM.exeAccess Request Information: Accesses: ReadData (or ListDirectory) Access Mask: 0x1
Conclusion
Ultimately, our goal of the Misconfiguration Manager project is to empower defenders with the same depth of knowledge that adversaries exploit. By implementing and testing these detections, organizations can better guard access to their implementation of Configuration Manager; ensuring they remain a reliable tool for system management rather than a vector for compromise.
Misconfiguration Manager: Detection Updates was originally published in Posts By SpecterOps Team Members on Medium, where people are continuing the conversation by highlighting and responding to this story.
First seen on securityboulevard.com
Jump to article: securityboulevard.com/2024/12/misconfiguration-manager-detection-updates/
![]()

