TL;DR Insurance companies host large amounts of sensitive data (PII, PHI, etc.) and often have complex environments due to M&A and divestitures Most breaches start with human error Fortune 500 companies rely on Microsoft Active Directory as a backbone for Identity and Access Management Attackers target Active Directory to move laterally and escalate privilege An Attack Path Management solution can proactively find and remove attack paths Insurance companies collect sensitive data”Š”, “Šthink medical history or credit card information”Š”, “Što fully understand the value of what they’re insuring and the risk they’re taking on. The same risk then applies to the protection and storage of sensitive data. In the hands of a bad actor, it’s a treasure trove for data brokerage on the dark web. Compounding the problem is that insurance industries are embracing digital transformation, creating apps that collect data and giving every policyholder a login to access their information. As they should! Insurance companies need to stay agile with the latest technology to speed up internal business processes and increase customer satisfaction. But the hard truth is that 68% of data breaches start with someone either falling for a social engineering scheme or leaking data by mistake.
Keeping a bad actor at bay in Active Directory
Many organizations rely on Active Directory to manage user access to other important company systems and resources. Misconfigurations and technical debt within Active Directory combine over time to create attack paths. These attack paths can allow adversaries to move through the environment with ease and blend in with administrative behavior. One of the most efficient ways to mitigate the risk of a breach is by proactively mapping and removing these attack paths. Insurance companies should focus on removing all attack paths to Tier 0 and other critical assets. A good Attack Path Management solution will prioritize Tier Zero attack paths, provide detailed remediations and continuously monitor to protect against regression.
Why insurers carry unique digital risk
Insurance companies often rely on legacy technology, and over time technical debt piles up, slowing down the speed of business. Additionally, mergers and acquisitions in the insurance industry increase the likelihood of adopting existing misconfigurations and generous privileges, while divestitures might leave a trail of digital backdoors after separating. The directory environment can become too entangled to sort out manually. And as mentioned earlier, the insurance industry is prone to collecting and storing sensitive data that makes insurance companies an attractive target for bad actors.
Attack Path Management enhances your security posture
Adding an Attack Path Management solution to your security stack accomplishes two goals: visualizing your complex environment and the relationships between systems, devices and users and finding potential attack paths to remediate.
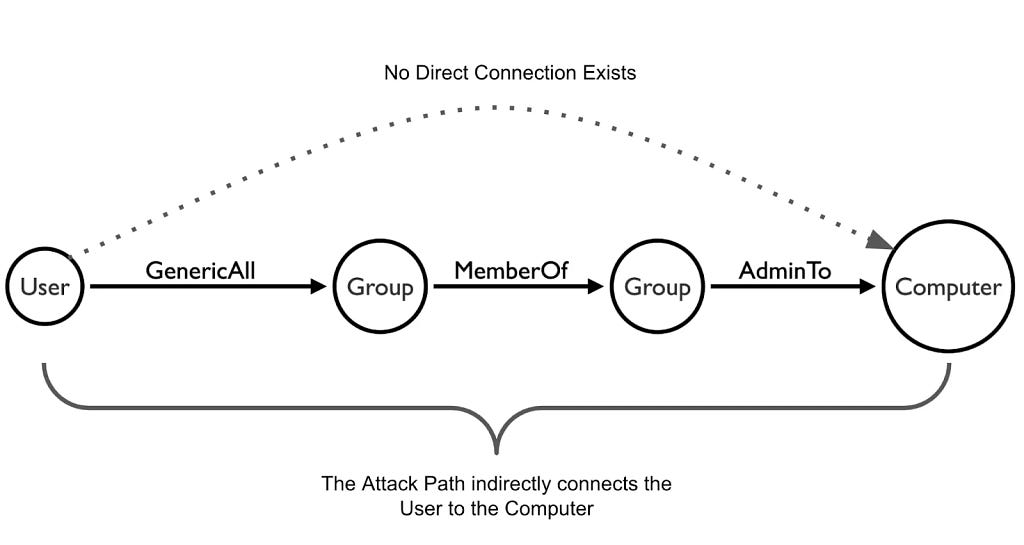
Over time, access permissions become difficult to track”Š”, “Šcontractors get temporary credentials, new applications require special permissions, and remote employees log in from personal devices. These small oversights changes can snowball into major security gaps. Choosing a tool that continuously scans your environment for new devices, users and permissions/configurations puts your blue team back in the driver’s seat when it comes to vulnerability management. You can stop reacting to threats and start proactively shutting down attack paths.
BloodHound Enterprise removes risk at the root
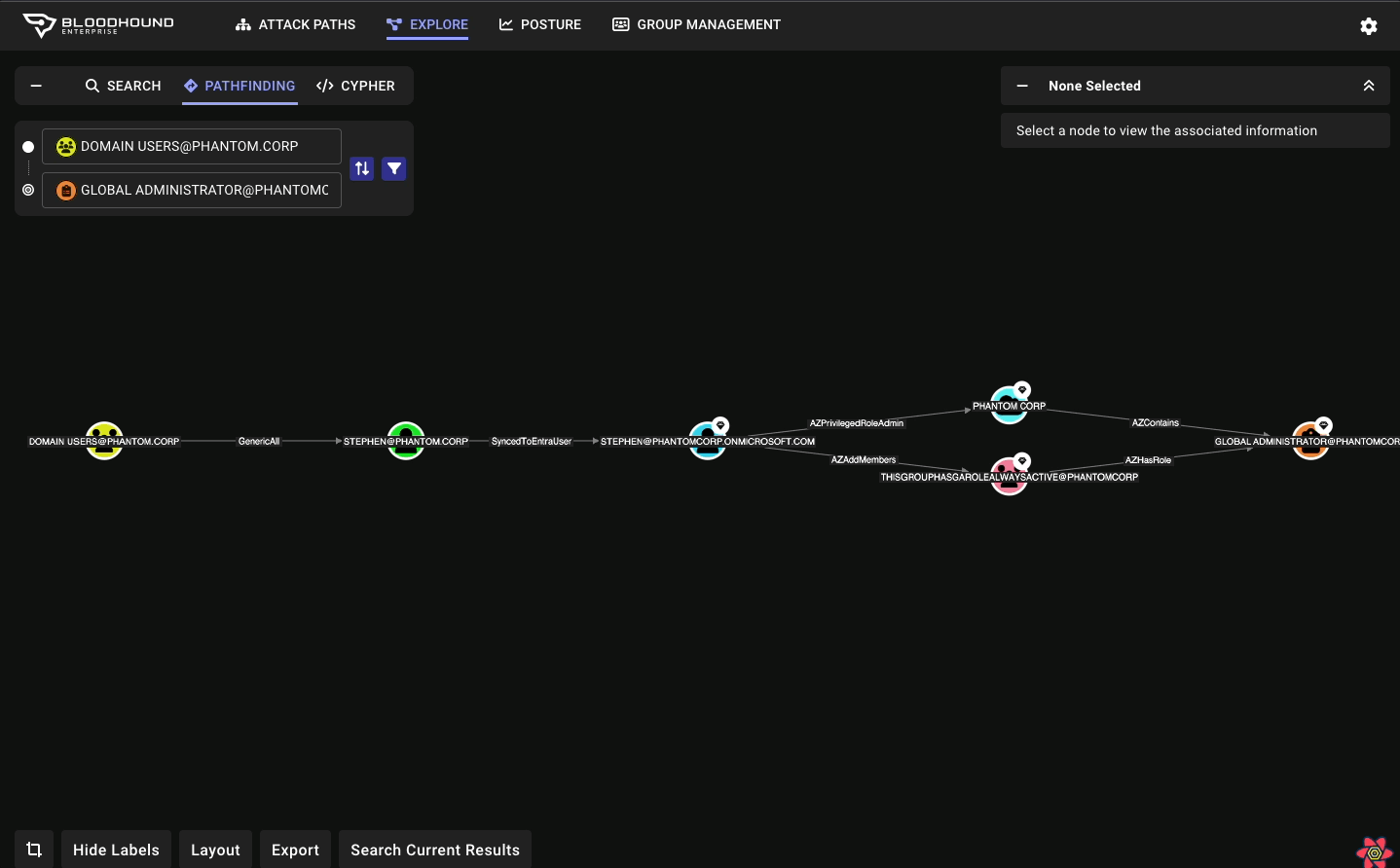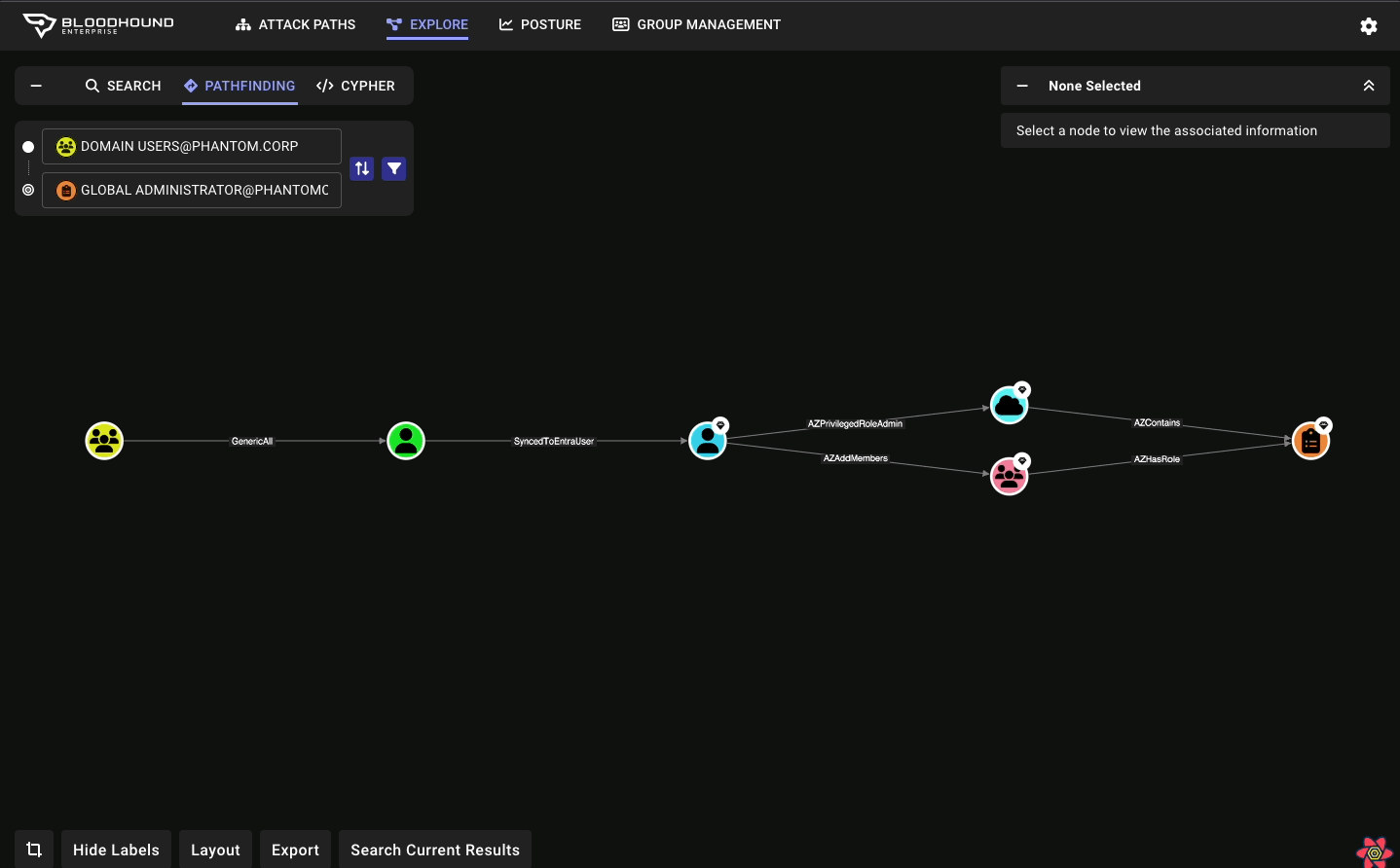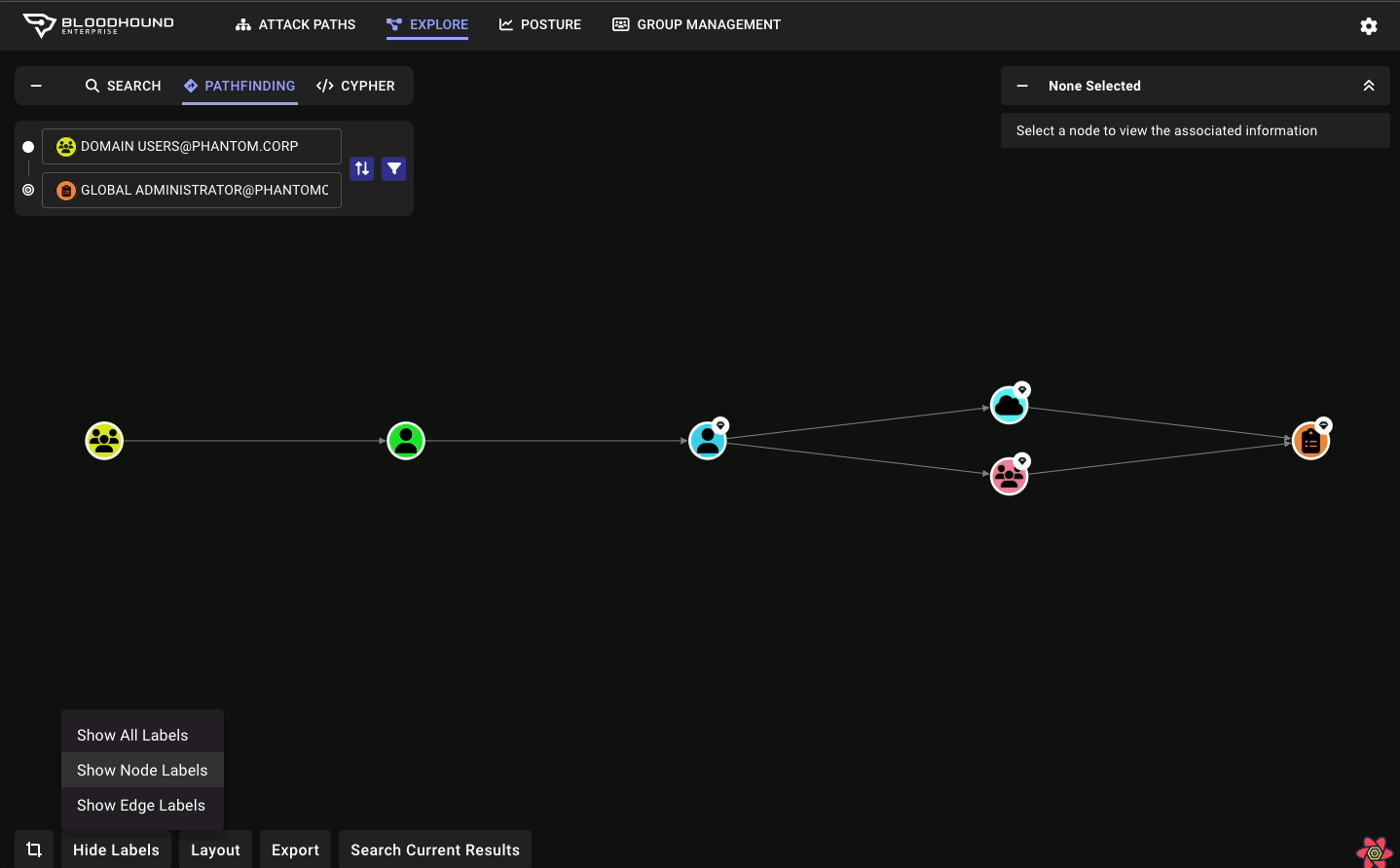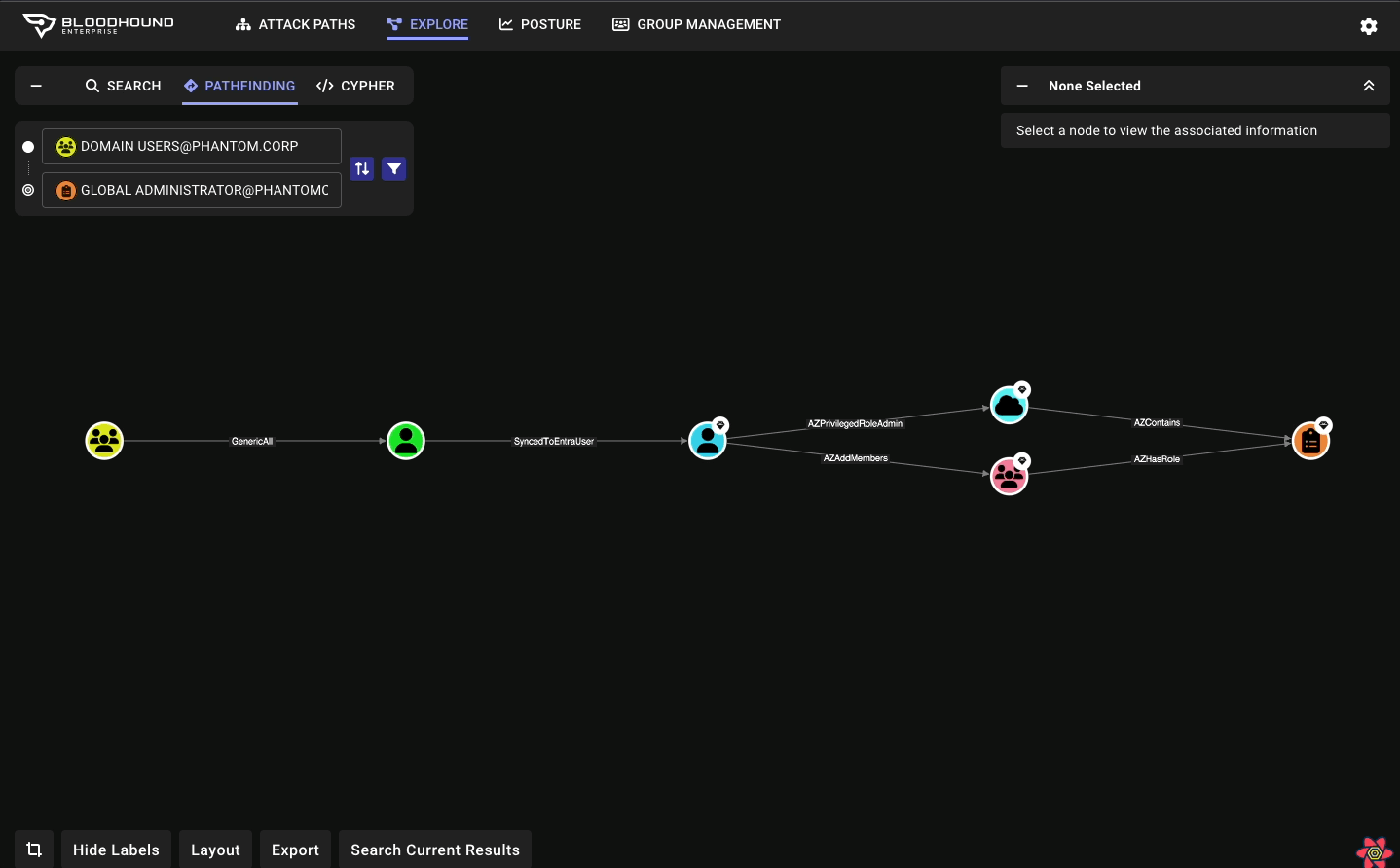
BloodHound Enterprise, the leading Attack Path Management solution, can help you quickly and effectively visualize, prioritize and remove attack paths without disrupting operations. You can remediate with confidence as BloodHound finds the most efficient choke points to sever thousands of attack paths, often with a single fix. Other benefits of BloodHound Enterprise include: Network visuals to help better understand complex directory environments due to mergers and acquisitions and divestitures Measure your Identity risk and exposure in Active Directory, Entra ID and hybrid environments Eliminate years of technical debt Continuously audit for new Identity risk introduced into your environment To learn more about BloodHound Enterprise and the problem of Identity-based attack paths click here. If you’re ready for a demo, reach out.
Insurance companies can reduce risk with Attack Path Management was originally published in Posts By SpecterOps Team Members on Medium, where people are continuing the conversation by highlighting and responding to this story.
First seen on securityboulevard.com
Jump to article: securityboulevard.com/2025/01/insurance-companies-can-reduce-risk-with-attack-path-management/
![]()

