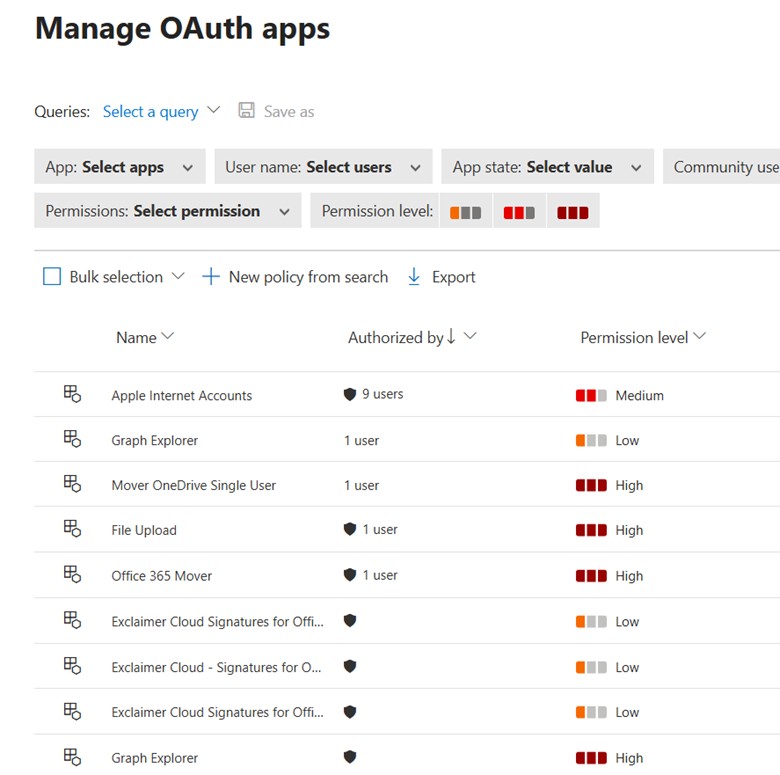
Set the filter to permission level “high severity” and community use to “not common”. Using this filter, you can focus on apps that are potentially very risky, where users may have underestimated the risk.Under Permissions select all the options that are particularly risky in a specific context. For example, you can select all the filters that provide permission to email access, such as Full access to all mailboxes and then review the list of apps to make sure that they all really need mail-related access. This can help you investigate within a specific context, and find apps that seem legitimate but contain unnecessary permissions. These apps are more likely to be risky.Select the saved query Apps authorized by external users. Using this filter, you can find apps that might not be aligned with your company’s security standards.
Filter on “last authorized” to review when an application has recently entered into your network. Then filter on the number of users and ensure that you review those OAuth applications that have few of users. Ensure you perform this review on a semi-regular basis.
 b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=150%2C150&quality=50&strip=all 150w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=300%2C298&quality=50&strip=all 300w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=768%2C763&quality=50&strip=all 768w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=701%2C697&quality=50&strip=all 701w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=169%2C168&quality=50&strip=all 169w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=85%2C84&quality=50&strip=all 85w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=483%2C480&quality=50&strip=all 483w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=362%2C360&quality=50&strip=all 362w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=252%2C250&quality=50&strip=all 252w” width=”780″ height=”775″ sizes=”(max-width: 780px) 100vw, 780px” />
b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=150%2C150&quality=50&strip=all 150w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=300%2C298&quality=50&strip=all 300w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=768%2C763&quality=50&strip=all 768w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=701%2C697&quality=50&strip=all 701w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=169%2C168&quality=50&strip=all 169w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=85%2C84&quality=50&strip=all 85w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=483%2C480&quality=50&strip=all 483w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=362%2C360&quality=50&strip=all 362w, b2b-contenthub.com/wp-content/uploads/2025/02/Manage-OAuth-apps.jpg?resize=252%2C250&quality=50&strip=all 252w” width=”780″ height=”775″ sizes=”(max-width: 780px) 100vw, 780px” />Susan BradleyNext, review the permission level for all OAuth applications, ensuring that you know and have authorized any OAuth application that has a high-permission level in your environment. Decide whether these applications still should be allowed the highest permissions in your organization.Review any app’s reputation in the industry and ensure that it’s widely installed. If not, review the type of application it is, it could be a backup app or such that may not have many users. Determine its purpose and review that the application only has permissions related to that intent.
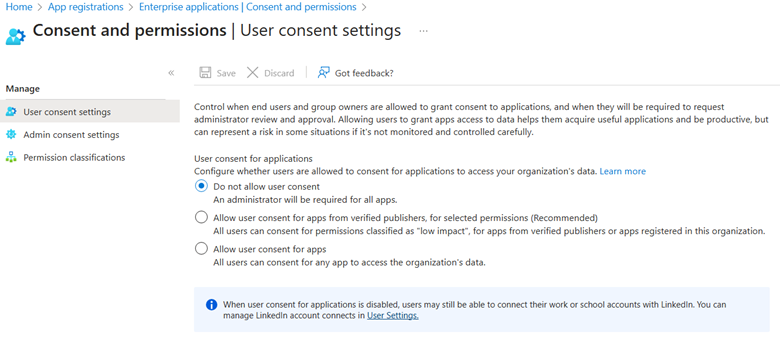
How to set up OAuth approval: Organizations should review if they can turn on administrative OAuth approval for apps that ask for Microsoft 365 information and access. As noted by Microsoft, you will need to log into EntraID in order to set this approval setting.Sign in to the Microsoft Entra admin center as a Privileged Role Administrator.
- Browse to Identity > Applications > Enterprise applications > Consent and permissions > User consent settings.Under User consent for applications, select which consent setting you want to configure for all users.Select Save to save your settings.
Depending on your business needs and risk analysis, you may want to opt to be more proactively secure and require administrative approval for all applications added to your network. Alternatively, you can adjust the permissions to allow users to automatically get authorization for applications considered “low impact”. These applications are from verified publishers or apps registered in this organization.I strongly recommend you do not choose to allow users consent for apps which allows all users to consent for any app to access the organization’s data.
 b2b-contenthub.com/wp-content/uploads/2025/02/OAuth-consent-and-permissions.png?resize=300%2C131&quality=50&strip=all 300w, b2b-contenthub.com/wp-content/uploads/2025/02/OAuth-consent-and-permissions.png?resize=768%2C335&quality=50&strip=all 768w, b2b-contenthub.com/wp-content/uploads/2025/02/OAuth-consent-and-permissions.png?resize=150%2C65&quality=50&strip=all 150w, b2b-contenthub.com/wp-content/uploads/2025/02/OAuth-consent-and-permissions.png?resize=640%2C279&quality=50&strip=all 640w, b2b-contenthub.com/wp-content/uploads/2025/02/OAuth-consent-and-permissions.png?resize=444%2C194&quality=50&strip=all 444w” width=”780″ height=”340″ sizes=”(max-width: 780px) 100vw, 780px” />
b2b-contenthub.com/wp-content/uploads/2025/02/OAuth-consent-and-permissions.png?resize=300%2C131&quality=50&strip=all 300w, b2b-contenthub.com/wp-content/uploads/2025/02/OAuth-consent-and-permissions.png?resize=768%2C335&quality=50&strip=all 768w, b2b-contenthub.com/wp-content/uploads/2025/02/OAuth-consent-and-permissions.png?resize=150%2C65&quality=50&strip=all 150w, b2b-contenthub.com/wp-content/uploads/2025/02/OAuth-consent-and-permissions.png?resize=640%2C279&quality=50&strip=all 640w, b2b-contenthub.com/wp-content/uploads/2025/02/OAuth-consent-and-permissions.png?resize=444%2C194&quality=50&strip=all 444w” width=”780″ height=”340″ sizes=”(max-width: 780px) 100vw, 780px” />Susan BradleyRequiring administrative approval can add a layer of overhead that may be hard for an organization to administer. But this overhead may be the difference between a secure organization and one that gets hit with business email compromise. Especially in this era of high cloud usage, identity is the edge of your organization.Review logs of the OAuth integration and ensure the access is appropriate on a regular basis. Once an identity has been compromised with the reuse of an OAuth token you’ll need to reset passwords, reauthorize two-factor authentication and possibly consider isolating that user account and setting up a brand-new identity.
On-premises Active Directory is also vulnerable: Lest you think that compromises of on-premises Active Directory are any easier to root out, guess again. A recent Microsoft blog post showcased how attackers are just as eager to go after Active Directory identities and attack those as well.Microsoft recommends tools included in 365 Defender to help identify your weak spots. Start by reviewing your Defender for Identity section of the Secure score and review the recommendations that appear there.Next, consider what lateral movements attackers can possibly make in your organization’s network. I reiterate again how important the use and deployment of the Local Administrative Password Solution (LAPS) is in helping to prevent ingress in the first place.This automatically manages the password for the built-in administrator account on Windows devices. The initial setup of a workstation is typically accomplished with an image and a common password. If the attacker is able to obtain the value of this shared password, they are then able to perform lateral movement throughout the network.Even with the use of LAPS, you could have other tools that have a similar shared password. Backup software often introduces the risk of a shared account across many assets that may introduce the risk of lateral movement.Take the time to review your cloud authentication as well as your active directory identity and the protections you have put in place. Then go back and start over and review them again. Constant monitoring and review are key to a properly secure organization.
First seen on csoonline.com
Jump to article: www.csoonline.com/article/3833826/how-to-configure-oauth-in-microsoft-365-defender-and-keep-your-cloud-secure.html
![]()

